Ransomware 2016 – How valuable is your data?
Wikipedia sets the inception of the first form of ransomware back to 1989 and with the evolution of technology ransomware has become one of the most dangerous forms of malware that has wrecked havoc on individual and business data alike. Although incidents have been reported as early as 1986, the latest versions of ransomware or cryptolocker as it is popularly known although there are different versions with different names are far more sophisticated. They not only infect the local machine but also infect removable devices and devices connected on the network. Are you or your organization prepared for this threat?
ran·som·wareˈransəmˌwe(ə)r/noun
Where does it start?
It can start from an infected usb stick, phishing email or a malicious/infected website. Maybe you connected an infected USB drive to your computer, or received an email which seems to be from a legitimate company with an attachment or a link directing to the infected files. The result in either case is that your files are encrypted and become unusable, you get a message on your screen that all your files are encrypted and you need to pay certain amount of bitcoins to get the decryption key in order to restore your files. Imagine this happening to a business with sensitive client information, financials, intellectual property etc which could lead to huge losses.
Ransomware has become a huge threat to personal and corporate data with over 90% of phishing emails containing attachments or links directing to the ransomware. The victims system is infected with the ransomware and all user files are encrypted. The most interesting part is that it does not encrypt all system files and only goes for user data with the most common extensions. The most common susceptible file extensions are:
..tif ,.gif ,.png ,.bmp ,.3dm ,.max ,.accdb ,.db ,.jpg ,.jpeg ,.raw , ,.dbf ,.mdb ,.pdb ,.sql ,.*sav* ,.*spv* ,.*grle* ,.*mlx* ,.*sv5* ,.*game* ,.*slot* ,.dwg ,.dxf ,.c ,.cpp ,.cs ,.h ,.php ,.asp ,.rb ,.java ,.jar ,.class ,.aaf ,.aep ,.aepx ,.plb ,.prel ,.prproj ,.aet ,.ppj ,.psd ,.indd ,.indl ,.indt ,.indb ,.inx ,.idml ,.pmd ,.xqx ,.xqx ,.ai ,.eps ,.ps ,.svg ,.swf ,.fla ,.as3 ,.as ,.txt ,.doc ,.dot ,.docx ,.docm ,.dotx ,.dotm ,.docb ,.rtf ,.wpd ,.wps ,.msg ,.pdf ,.xls ,.xlt ,.xlm ,.xlsx ,.xlsm ,.xltx ,.xltm ,.xlsb ,.xla ,.xlam ,.xll ,.xlw ,.ppt ,.pot ,.pps ,.pptx ,.pptm ,.potx ,.potm ,.ppam ,.ppsx ,.ppsm ,.sldx ,.sldm ,.wav ,.mp3 ,.aif ,.iff ,.m3u ,.m4u ,.mid ,.mpa ,.wma ,.ra ,.avi ,.mov ,.mp4 ,.3gp ,.mpeg ,.3g2 ,.asf ,.asx ,.flv ,.mpg ,.wmv ,.vob ,.m3u8 ,.csv ,.efx ,.sdf ,.vcf ,.xml ,.ses ,.dat
The above extensions are renamed to .mp3, .locky, .micro, etc depending on the type of ransomware that your system has been infected with. Once the encryption process is complete your computer displays a message with:
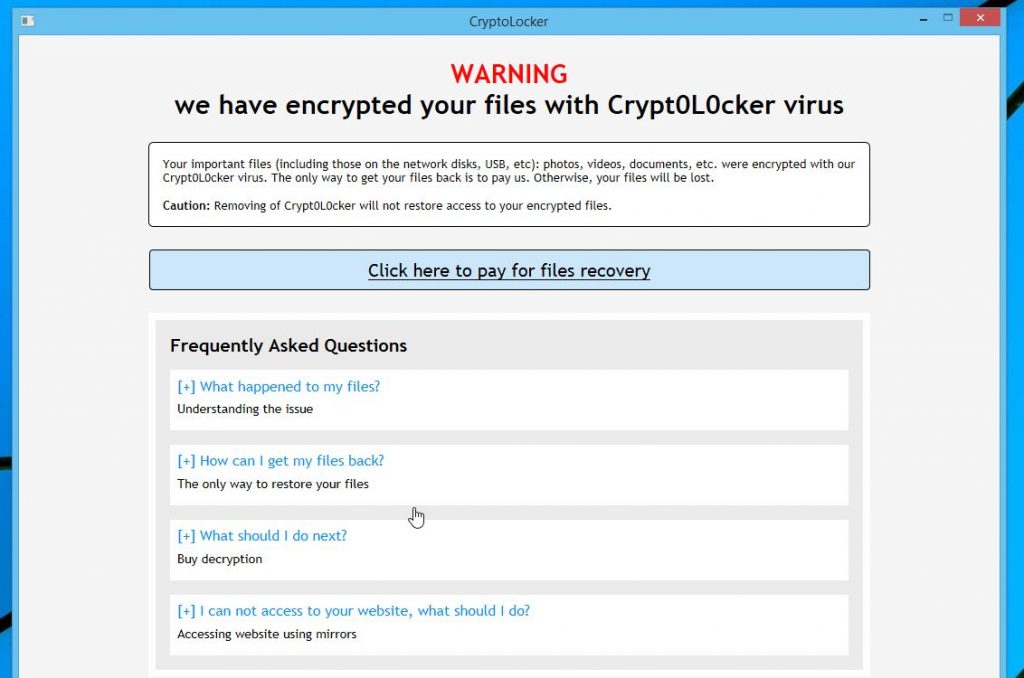
The above screen might be different in appearance depending on the kind of ransomware that the system is infected with but will convey a similar message.
Precaution is better than cure
As the old saying goes precaution is better than cure. The statistics are pretty straightforward, over 80% of ransomware infections are caused by end users themselves and over 75% incidents are caused by users on a corporate network. In order to fight this menace effectively there are a few guidelines that can be followed to minimize infection risk:
- Security updates: Software updates for operating systems and software’s are a must. Yes they take time and yes you need to restart your computers, but if you keep your systems upto date the updates will be less time consuming and there will be lesser restarts. Software upgrades provide necessary security patches and upgrades to the existing software systems and should never be ignored. These software updates close security vulnerabilities in the software environment making it harder for external threats to cause damage.
- Antivirus & Anti malware: Always use antivirus and anti malware software on your computers. Keep them updated and run thorough scans weekly to keep your system clean from everyday infections and known malware.
- Data Backup and Restoration: Systems should run volume shadow copy services at all times and regular data backups should be made of all critical data. Volume Shadow copy keeps copies of your documents and drives as they are modified. System backups can be made in various forms on offline media or cloud storage. Setting up shadow copies and backups properly will ensure that in case your system is infected you will always have the latest copy of your data.
- Limit user permissions: Not all users require administrative or domain privileges. Limiting user permissions and implementing proper user group policies can help limit the damage from infections to the particular user, preventing network wide infections.
- User Awareness: Of the above mentioned guidelines, nothing is more effective than user awareness. Understanding and screening suspicious emails, instructing users on proper browsing habits will go a long way in keeping your systems, networks and data safe. Not only that it is a much more cost effective method than having to deal with the consequences of lost data and productivity.
What to do if your system is infected with ransomware?
Disconnect network cables, removable media and shut down the system immediately so that the infection does not go further than the local machine and does not cause further damage to the files. In case all the files have been encrypted, clean up the system and restore file back ups. Although we are strictly against paying the ransom to get the decryption keys to restore your information, if you do decide to go this way please keep in mind that there is no guarantee that you will be able to restore your data. Moreover paying the ransom will only support the creators of the ransomware in continuing their task.
At Logical Edge Services Inc we offer customized security solutions for your business and home networks. Contact us today to find out how Logical Edge Services can help you with securing your organizations data, systems and network from ransomware and other external threats.

